[The following is a post written at my invitation by Professor Duncan Buell from the University of South Carolina. Curiously, the poll Professor Buell mentions below is no longer listed in the list of past & present polls on the Courier-Journal site, but is available if you kept the link.]
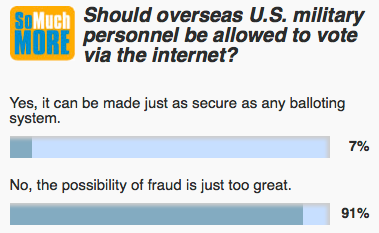 On Thursday, March 21, in the midst of Kentucky’s deliberation over allowing votes to be cast over the Internet, the daily poll of the Louisville Courier-Journal asked the readers, “Should overseas military personnel be allowed to vote via the Internet?” This happened the day before their editorial rightly argued against Internet voting at this time.
On Thursday, March 21, in the midst of Kentucky’s deliberation over allowing votes to be cast over the Internet, the daily poll of the Louisville Courier-Journal asked the readers, “Should overseas military personnel be allowed to vote via the Internet?” This happened the day before their editorial rightly argued against Internet voting at this time.
One of the multiple choice answers was “Yes, it can be made just as secure as any balloting system.” This brings up the old adage, “we are all entitled to our own opinions, but we are not entitled to our own facts.” The simple fact is that Internet voting is possible – but it is definitely NOT as secure as some other balloting systems. This is not a matter of opinion, but a matter of fact. Votes cast over the Internet are easily subject to corruption in a number of different ways.
To illustrate this point, two colleagues, both former students, wrote simple software scripts that allowed us to vote multiple times in the paper’s opinion poll. We could have done this with repeated mouse clicks on the website, but the scripts allowed us to do it automatically, and by night’s end we had voted 60,000 times. The poll vendor’s website claims that it blocks repeated voting, but that claim is clearly not entirely true. We did not break in to change the totals. We did not breach the security of the Courier-Journal’s computers. We simply used programs instead of mouse clicks to vote on the poll website itself.
In one case, the script was a bash script that looped a specified number of times and issued a curl command. My colleague’s comment was:
I started by looking at the source code of the website, which is possible with any browser. The poll in question used a HTTP form to submit the result, and only using cookies to prevent duplicate voting. One quick Google search later, I was reading a website about how to submit form data with curl (a linux utility that allows you to send all kinds of HTTP requests from a shell). From there, it was a simple matter of tinkering with the curl command until it submitted the result I wanted, and then looping it to run a large number of times. Curl doesn’t store or use cookies unless you explicitly tell it to, so it avoided the poll’s duplicate voting system entirely.
In the other case, what we had was a simple HTML script to enter data into the web form, and the script was run repeatedly with iMacros in Firefox.
Each of the scripts was done in about 30 minutes start to finish, and then run on four computers at home (2 + 1 + 1 for the three of us). When we started, just after dinner, the vote was 255 for, 90 against, and 146 “I’d have to be convinced”, with a handful of “no opinion” votes. By 10:30pm, we had collectively voted “no” about 9000 times. By Friday morning, we had voted more than 60,000 times and the poll was running 13 to 1 against.
This was a simple online poll that was easily compromised. Internet voting vendor software will be harder to compromise, but this shows that computer security is hard and claims must be proved. Before we entrust critical public functions such as voting to such software, the public deserves a solid demonstration that such claims are truly substantiated, and policy makers need to be schooled in a proper skepticism about computer security. That has not yet happened.
There is an irony in hacking an online poll about whether voting can be hacked. But it points to a much-needed dialogue between policy makers and computer security experts. Elections are too important to be entrusted, without proof, to the marketing hype of an Internet voting company. The nation’s real elections should be decided by the voters in the nation’s jurisdictions, not by whichever entity – foreign or domestic – happens to have the best software bots running on any given biennial Tuesday in November.

I agree with people being able to vote, but voting online I don’t think it is secure as you going to a destination and casting your vote. Casting your vote via internet is not really a safe way because anyone I feel can hack into the system and do what they want to the votes that has being cast. If it was to happen the person or people that created the site I believe they might have to get a trusted site to or persons to get the information to whom it need to get to. In thinking about the internet and computers a person is left to think about the security of Confidentiality, Integrity, and Availability.
Internet voting security is indeed a must. But how can this happen? Many people have doubts regarding this system since no one will ever know if anyone would make any alterations with regards to the voting process. But for me, I’m still hopeful that with the efforts of the people who made this, everything will be perfect and that it will be assured that nothing comes in between that could alter the electoral process. And not just any wishful thinking. Thanks!
–SurveyAndBallotSystems.com
And my first thought to the poll? Invalid and biased polling questions. No way would I say “Yes, it can be made just as secure as any balloting system.” But no way could I possibly say “No, the possibility of fraud is just too great.” Nor the other answers given. None of the answers are viable from my perspective and they all show a bias by the ones conducting the poll.
I like your article as to point out how you rigged the poll, that is cool. But an online poll is NOT a balloting system, and I highly doubt they created it to be, even if they claimed it didn’t allow duplicate voting.
Here is my question, to minds far superior to mine. Is the qualifier “at this time” at the end of the first paragraph a valid qualifier? Meaning, will there ever be a time?
I would have answered the question (and maybe been motivated to outscore your voting with my voting) if one of the answers was “”Yes, BUT ONLY if it is made to be as secure as any other balloting system.” (emphasis added on the change).
It seems to me, the writings of many on here talk much about security, and often about voting security. I ask, couldn’t such system be made to be as secure as others? Not to say it is now, as obiously the poll wasn’t.
With my little study, seems that anything done over HTTP is not going to be secure for the purposes of such voting mechanisms because HTTP was not made to be such a system, it was created to disseminate information. BUT, HTTP is not the only protocol that runs over the connections we call “the Internet.” In fact there are many protocols. Could a system (a new set of protocols) be created to run over the TCP/IP stack (i.e. the Internet) that is secure?
Maybe, and maybe not. I don’t have the technical expertise to claim one way or another. And, so I ask you, those who do have more expertise. Is the “at this time” a qualifier, could the answer be “yes, when we have perfected a secure balloting system over the Internet, but not until then”?
What a worthless demonstration. Of course anyone can use iMacros or write a few line of Javascript to do what the good Professor did. But did he ever hear of a Captcha? All he showed was a trivial attack that has a trivial defense. I hate those things, but most sites use them who want to confirm they likely have a real human on the other end. Of course, there are black market Captcha human powered operations, but as I said, it is a trivial defense that would have defeated the attack that the good Professor mounted.
The three elements of computer security are Confidentiality, Integrity, and Availability (CIA). In this case confidentiality is obviously addressed with some form of encryption. I think either standard encryption will do or the US military can have a trick or two up its sleeve in that area. Also military personnel have access to relatively secure military networks: “voting from the Internet might not be quite accurate because they could be using a secure subnet.”
Most important is authentication. The military has numerous forms of authentication, including of course blood type and DNA in case of being wounded or blown into itty, bitty little pieces. I do think the military might be in a good position to enforce whatever biometric they desired or requisite piece of knowledge. The greatest threat would be either on the end nodes being compromised by mal-ware which would be at worst a one-at-a-time threat, not multiple voting. The servers would also be at risk for the usual and not so usual sorts of attack. And yet we live with these levels of risk for commercial transactions and other sensitive systems. I think those who would deny the right to vote electronically have the burden of proof to show the devastatingly unique nature of online voting systems. Compared to the potential threat to mail in ballots, electronic voting has a measure of tough defenses. But the good Professor did not make it out of Kindergarten in that regard with such a lame example.
BTW, for those who might be interested, “hacking” the poll site required zero programming. And I mean “zero”. All you had to do was set your browser to “private browsing” mode, and you could cast as many votes as you want, since it doesn’t keep cookies. Or use multiple browsers. Or any number of other methods – I cast a half dozen votes to convince myself that I could without writing any code…
One would assume that a real voting system would be far more resilient. But of course without any open testing, and without any standards to test against and no certification process, one has to rely on the vendors’ statements, such as the claim in Kentucky that they used “military grade security” (by which they apparently meant SSL). And there lies madness.
I replied with a question below before reading other posts. I see you address part of my concern here though not an answer to my question. Rather it appears you qualified your rant with the statement “one has to rely on the vendors’ statements.”
And, in that case, I would also have to answer NO to such voting. I trust no one. But, then I don’t even trust regular voting in my state. Up until the last two elections I am 100% certain my votes were never counted, and even though there is some chance that my votes have been counted the last two elections, it is still very likely that they were not.
It reminds me of my early days on the Internet, where I had worried of certain dangers. I got on the internet through an ISP that “proxied” all requests so as to block inappropriate and/or malicious web traffic. As the proxy was maintained at the ISP and I dialed in, there was simply no way around it, or at least I had no knowledge of any way around it at that time. But about a year and a half later, my ISP decided that they would instead contract with a “filter software” company and instead of proxying all traffic, they licensed the filter software for all their users to whom wished to install it.
The claims by the filter software developers were that there was no possible way around their system because… well they gave enough away of their process in their “because” statement, that it took me a whopping 10 minutes to bypass and test the bypass to their software. And website that were known to be blocked I was able to get to with very little trouble. Another 2 hours and I was able to fully cover all my tracks that the software had ever been hacked so that at any time, the software could be “re-hacked” and “un-hacked” with simply a double click and a reboot each way.
No, I will not trust any vender that “claims” they are secure. But, I still question, isn’t there a way to do it securely in such a way as to ensure via peer review processes that the security is valid?
Many of the comments here are indeed correct. The simple poll software was not secure against some corruption, and it was easy to show it was not.
That gives us one data point: low grade software, with low grade security. For internet voting, we would want very high grade security. So can we quantify that? Have the vendors released their system for testing (and hacking?) by one and all?
Perhaps we should imagine a NIST process similar to that which led to the adoption of AES. All and sundry get to submit their software for testing in an open contest. Everyone gets to bang on all the proposals as hard as they would like. The best solutions make it to the second round, where another round of testing takes place. And again. And, as with AES, all the details are public knowledge. No security by obscurity, because one has to assume The Bad Guys have co-opted someone on the inside.
I am reminded of when the safes were installed in the offices in my previous job. On the side of the safe it said something like “Certified against 60 minutes of sustained attack.” One of the more central safes in the document room had a larger number of minutes. Up until then I had never thought of that sort of thing, but it made sense.
This might lead to a real quantification of the risk and the security. We know that the poll software would perhaps just barely be able to say “Certified safe against the lunchtime attack of the Boiling Springs Elementary School Computer Club.”
Of course, what we would really want for voting would be something that would read “Certified safe against a six-month attack by the People’s Liberation Army/Tsinghua University Cybersecurity Attack Team.” But I doubt we would get that information delivered to us willingly by the Chinese government. And therein lies part of the problem. We just don’t know, and we just wouldn’t know.
For what it’s worth, I find myself in agreement with those who point out that the “achievement” here has been to demonstrate that piece-of-crap software can be insecure, which demonstrates zip about theoretically non-crap software.
But that’s not the critical issue, and this entire event has been a diversion.
The critical issue is that there is no way for the general public to confirm that internet voting is working properly, and that their votes, therefore, have been properly recorded and tabulated. Also, of course, there is no way for election authorities to confirm that an individual voting over the internet has done so in an environment of enforced privacy, so that there is no way for anyone to purchase their vote or threaten their vote.
If no reasonable alternative to internet voting were available, the lack of easily understood security might be an acceptable situation, given that the public could ask for a consensus of computer science professors, and some might be reassured by the consensus. Military voting from front lines might be exactly such a situation. I’m not sure how the potential privacy issues are addressed.
However, for the general public, an alternative has been and always will be available. It involves people going to polling places distributed across the country, marking a piece of paper, depositing that piece of paper in a box monitored by witnesses in the room, and having the votes on that piece of paper tabulated in a way that human beings can verify. It’s old tech, which is often the best tech.
The fact that this old tech involves large numbers of people each tackling their share of a naturally distributed and parallel IT problem does not make it bad. In my opinion, it is yet another reason this old tech is so superior. Citizens in a democracy *should* in my opinion, be hands-on in the eleciton process. More eyes is better. Efficiency is the holy grail of capitalism, not democracy.
“The critical issue is that there is no way for the general public to confirm that internet voting is working properly, and that their votes, therefore, have been properly recorded and tabulated.”
[citation needed]. I am skeptical that there is any proof that secure, anonymous, verifiable internet voting is necessarily impossible. Check the ThreeBallot[0][1] protocol. It’s anonymous but verifiable voting system, designed to be usable with paper-based ballots, but it certainly could be implemented electronically.
“Also, of course, there is no way for election authorities to confirm that an individual voting over the internet has done so in an environment of enforced privacy, so that there is no way for anyone to purchase their vote or threaten their vote.”
That’s the case with any absentee/postal/other remote voting system. Are you suggesting that we stop allowing those votes?
[0] http://people.csail.mit.edu/rivest/Rivest-TheThreeBallotVotingSystem.pdf
[1] https://en.wikipedia.org/wiki/ThreeBallot
Karellen,
[1] I didn’t suggest such a proof existed. There is a difference between a group of computer scientists asserting that something is mathematically proven to be secure and verifiable and the general public therefore accepting that it is secure and verifiable. I am completely unqualified to offer an opinion about the former, but as a member of the general public I am not ready to trust the opinion of computer scientists or politicians that an invincible Maginot Line has been installed.
[2] Yes, I am suggesting that remote or absentee voting is inherently unacceptable when alternatives exist. If enforced privacy is a serious concern in a voting system, then absentee voting should be restricted to those who cannot reach a polling place during an election window. Its use should be rare, but not necessarily never.
Regarding Three Ballot, here is an extract from the Wikipedia entry:
“In the ThreeBallot Voting System voters are given three blank ballots, identical except for a unique identifier. To vote for a candidate the voter must select that candidate on two of the three ballots. To vote against a candidate (the equivalent of leaving a ballot blank in other systems) the voter must select that candidate on exactly one ballot.”
Do you understand, karellen, that many voters do not properly fill out their current paper ballots?
Do you have any idea of how inconceivably f’d up an election would be if the instructions included anything like the sentences above? It’s great that brilliant minds are always probing for what can be accomplished, but what can be accomplished in theory is a very different thing than what can be accomplished in a real-world election.
As someone worried about the ease of which the technologically “super savvy” can drastically effect those who are not as technologically literate, I see where you are coming from. It’s easy to fall into the trap of the “Liberty thesis” when it comes to the internet and the services it provides. It would do users some good if they realize that the internet is not always the freeing/liberating entity it may have been touted as during my childhood in the 90’s. However, I seem to also agree with the general consensus of commentators here that being unable to do so at the moment does not mean that it can’t be done. Though technology may not always be liberating, that doesn’t mean it can never be. It will take a lot of work and if we intend for those military personnel overseas to continue feeling like they can support the political process at home, we’ll need work on it. Paper-based methods can only go so far in a world that is quickly becoming interconnected. We’d have to learn and work on the systems that would be implemented, but I think that it is a goal we could reach.
Say hi to Weev when you get there…
Congratulations, you’ve shown that the online poll software for a local newspaper’s website is not secure enough to run a real vote.
That does not disprove “Yes, it *can* be made just as secure as any balloting system”; it just proves that one particular piece of home-grown balloting software happens to be crap.
Secure votes can be, and are, run over the internet. The Debian[0] project does secure internet voting. There are published protocols for cryptographically secure internet voting[1]. Yes, you need to get someone who really understands cryptographic protocols to design and/or audit the system. Someone like Bruce Schneier, Dan Kaminsky, or someone equivalent who not only is known to know their stuff, but has the connections and clout in the security industry to be able to get others to double-check their work, and (more importantly) knows *who* is worth getting to double-check their work. And you need to be able to tell Premier Election Solutions (formerly Diebold), and the other current purveyors of (crap) electronic voting systems to go jump off a cliff.
It is possible to make internet voting just as secure as any other balloting system. No-one (AFAICT) has implemented it for governmental elections yet, and if no-one does then it’s not worth doing insecurely instead, but that doesn’t mean it *can’t be* as secure.
[0] http://www.debian.org/
[1] e.g., found with 2 minutes of Googling (even if the formatting is wonky), http://www.drdobbs.com/secure-internet-voting-with-perl/199102023
The debate over online voting has been fairly one sided because the industry does not have a 501(c) to carry its water. The industry has been slow to respond for fear as being seen as “shills” for their product. For a business to be successful they must produce a product that meets the need, is safe at any speed, and provides value for the dollar. Businesses that make products that do not meet these criteria do not last long. Academics and industry are like the chicken and the pig at breakfast: The chicken is interested, but the pig is committed. Let me speak on behalf of the committed industry.
As an academic I would have expected Professor Buell to have observed the tenets of information literacy, but instead he makes baseless assertions and then draws an analogy between a newspaper survey and rigorously tested, high security online voting software. Normally I would treat this with the contempt it deserves, but due to his claim to academic credibility his misdirection must be addressed.
The ease with which the newspaper’s poll was hacked is in no way indicative of the security provided by the professionals of my industry. We who work routinely with advanced cryptographic protocols and digital verification tools look upon those survey instruments much as an F35 pilot looks upon a Piper Cherokee. To cite the compromise of a survey in an effort to cast aspersions on online voting is a bald attempt to mislead the public. I believe the public is smarter than that. What is truly ironic is that an academic allowed his students to undertake a project that had the potential to cause a business harm, i.e., compromising the integrity of the Louisville Courier-Journal by purposefully deceiving its readership. Not only is that academically indefensible, but I would be surprised if were not actionable.
Dan: Which assertions were baseless?
I read the conclusion as “This little survey thing is not in the same league as professionally secured systems, but it made a claim and we disproved it. Professionally secured systems will also need to prove their claims.”
If you read it as “your product will be easy to hack” then I have to wonder who really isn’t observing the tenets of information literacy.
C’mon now: you could make internet voting from overseas just as secure as any other ballot method. Sure, you’d need to build special-purpose computers from trusted sources on both ends and hand-carry them to the overseas voting places and develop a key infrastructure also based on physical transportation under guard to verify each voter. Or maybe something even harder. But you could do it…
Oh, that wasn’t really the question?