Five years ago I described a serious security flaw in the design of all-in-one voting machines made by two competing manufacturers, ES&S and Dominion. These all-in-one machines work like this: the voter indicates choices on a touchscreen; then a printer prints the votes onto a paper ballot; the voter has a chance to review the ballot to make sure the right choices are printed; then the machine sends the ballot past an optical scanner to record and tabulate the votes. Then the mechanism drops the paper into a ballot box where it is saved for recounts or audits.
The reason we have paper (in addition to the optical scanner’s computer-count of the votes) is for our protection, in case the software in the voting machine is hacked. The votes printed on the paper and seen by the voter, can be seen again by the humans performing the recount or audit.
The fatal flaw is having the ballot printer in the same paper path that goes from the voter to the ballot box. That’s because the machinery (printer, scanner, motor-driven rollers) is controlled by the software, and if the software is hacked (replaced by fraudulent software) then the software can make the machinery do things “out of proper order”. In particular, after the voter approves the ballot and touches the “cast-vote” button on-screen, the software is supposed to convey the ballot past the scanner into the ballot box; but hacked software can direct the machinery to take a detour past the printer, where additional votes are printed on to the ballot that the voter did not approve.
This design flaw affects the Dominion ICE and the ES&S ExpressVote and ExpressVoteXL. We explained this problem in section 8 of our paper, Ballot-Marking Devices Cannot Assure the Will of the Voters, by Andrew W. Appel, Richard A. DeMillo, and Philip B. Stark. (Election Law Journal, vol. 19 no. 3, September 2020; non-paywall version here)
It seems that the engineers at ES&S read our paper, because they’ve released a redesigned paper path for the ExpressVoteXL that they claim fixes the problem. They produced this video that states their claim. Unfortunately, they’re wrong: it doesn’t fix the problem.
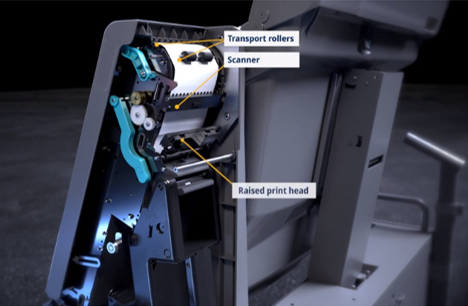
Their claim is: they have a new “one-way bearing” on their platen roller. It’s mechanically impossible for the “platen roller with one-way bearing” to print while the paper is moving down; mechanically it’s only possible to print while the paper is moving up.
These engineers have failed to “think like the attacker”. Their own software, after the voter has approved what’s printed on the ballot, would only direct the machinery move the paper downward past the scanner and print head. So they fail to consider how hacked software could behave differently. In particular, fraudulent vote-stealing software could move the paper down past the print head, then take the extra step of moving it back up, while printing unauthorized votes on the paper; then move it down again toward the ballot box.
In my opinion, the newly designed paper path, with the “one-way roller”, is just as flawed as the ExpressVote XL’s previous design. Either way, fraudulent software can print additional votes onto the ballot after the last time the voter has had a chance to see the paper. Therefore, ExpressVote XL ballots cannot be considered “voter verified”.
The ExpressVote and ExpressVoteXL have another really big security hole, that their new “fix” also does not fix. The votes that count are the ones encoded in the barcode (which the voter cannot read), not the ones printed in plain text (which the voter can read but usually doesn’t bother to read). The optical scanner reads the barcode, not the plain text. So voters can’t meaningly verify the real votes. Supposedly that could be addressed by an audit of the paper ballots–but many states that use (or are considering) the ExpressVoteXL (New York, Arkansas, Tennessee, …) have very weak audits that wouldn’t reliably catch cheating. And even worse, some election administrators think they can “audit” the paper ballots by running them through a different scanner (from ClearBallot)–but that scanner also reads only the barcode, which the voter has never been able to verify.

I recently used and ExpressVote system again. I am starting to get paranoid and the fact the entire tabulation is based on the bar codes is very misleading.
Over the last few years i have started to see small blemishes in the bar codes both when i come in to get my ballot (the code that tells the machine which partisans on the touch screen). To most recently almost all of the bar codes to have some or significant clarity issues. I find this of concern for the following reasons:
1) my vote literally is the bar code
2) the thermal paper print quality is intended to be crisp and accurate
3) some of the bar codes are very thin and i have seen imperfections that cause me pause
4) its uncommon a basic UPC scanner at a grocery store or general retailer would ever be able to read what i saw
5) when i questioned poll workers they told me to not worry about it
6) when asking for more information i was told i cannot take any evidence of the bar codes
Look, i want to not even post this. however i find it odd and problematic a simple bar code that has one way or another not been visually clear is my vote. The fidelity of a camera and how someone activates an apple watch is incredible.
I do not know the answer nor do i want to believe my vote is not being counted or at worst being manipulated… how can i even know a random set of bars actually equals my vote, one cannot.
Our trust is blind and corporations are greedy. Let’s scrap all this tech and get back to a paper ballet with punch holes. Try and doctor that!
also even nasa is transparent with single points of failure. there are too many
Appel’s point is that the “ExpressVote XL ‘fix’ doesn’t fix anything” and he’s made it. The EVXL moves the ballot paper so fast that a reversal would hardly be noticed — and if it were, voters wouldn’t know it’s an issue. And if they did, they couldn’t prove it happened or do anything about it. The paper should not pass by the print head after the voter approves it. That’s just poor design.
ES&S’s responses are telling. Supposedly there are methods for voters to validate the barcodes, e.g., “Philadelphia produces a code book to allow voters to validate the barcode selections”
As it happens, I have voted on the EVXL in every election since it was introduced in Philadelphia in 2019 — that’s eight times — and documented every aspect of the experience. Also, I’ve attended the great majority of Phila. Board of Elections meetings for nearly five years, watched the videos of those I missed, and read all the pollworker training materials and I think every piece of documentation they’ve published. I have never once heard of such a code book. If it exists, it’s locked away somewhere.
And what is this about “comparing the cast vote records to the printed text,” reading the card into a precinct tabulator and view the printed report and re-reading the card into an XL? None of these are possible unless the tabulation mode is turned off. Even if Philadelphia had precinct tabulators, the EVXL keeps the card behind a window. You can’t get it out to do any of these things. Only in pure BMD mode could these be possible, meaning that a purchasing county would need not only the EVXL but precinct tabulators. So this extraordinarily expensive system would be even more costly.
Then you’d have to pretend that voters would actually check — a step that few actually do. The whole validation problem goes away when voters fill out a ballot with their own hand. For those who can’t, accessible alternatives are required. But the EVXL is a poor choice for that, too: The Pa. Dept. of State, a staunch backer of the EVXL, found that “None of the participants [in its accessibility test group] were able to verify their paper ballot on the XL.” (More: https://docs.google.com/document/d/1nxoIdTyMfprRjIaI7hZuckarJEIJnB6wtbZB7rM0BnE/)
The EVXL is no way to earn the voters’ trust. It’s nothing more than an overpriced Rube Goldberg machine, designed to separate voters from their votes and foolish jurisdictions from their money. Not to say corrupt…plus ça change, plus c’est la même chose.
As a Democrat user of the XL system, I am profoundly disappointed that Andy Appel has effectively become the new Mike Lindell for the Democrat party.
He lives in a science fiction world, as many if these silly academics do. He lives in the hypothetical world, not in the real world. In the real world, in order to pull off a hack like his fantastic and delusional scenario describes, Andy and his so-called “sophisticated hackers” would have to gain illegal access to the warehouse where machines are stored, bypassing alarms, cameras and locks. Not impossible of course. Simultaneously, he would have to gain illegal access to the election management system, bypassing all of the same security. Then, he would somehow have to bypass Microsoft bitlocker. I don’t care what Andy says, if he tells you that bitlocker can be hacked he is flat-out lying. It has never been hacked and cannot be hacked with today’s technology. So if you successfully break into the warehouse and miraculously break through Microsoft bitlocker, then he’d be immdediately praised by Microsoft as the greatest hacker of the 21st century and they’d pay him millions.
In addition, the hacker would have to intuitively understand how to precisely get the software hack to perfectly line up with the firmware hack. Andy will say this is easy because he knows he’ll never have to prove it, a common behavior pattern of science fiction nerds and people who live in the world of fantasy. Finally, somehow this hack would have to be performed at scale (across perhaps thousands of machines that are not networked, thereby requiring the “sophisticated hacker” to access each and every machine individually) with a 48-96 hour timeframe to avoid being detected in the logic and accuracy test performed by each county.
In New Jersey these machines work beautifully and voters love them. Andy further likes to ignore the voter disenfranchisement inherent in the hand gmarked paper ballot voting process. Anywhere from .5% to 3% of votes marked on a ballot by hand are ultimately not counted due to overvotes and poor marking of the ballot. Andy doesn’t care that studies have shown that our most vulnerable voters (low literacy and low vision but not blind voters) are the ones most prone to these mistakes that cause their own vote to be disqualified. Andy doesn’t actually care about votes being counted. What he really cares about is scaring the hell out of the general public to enhance his own profile.
Does he remind you of any crazy Republican you’ve heard of? Check the first paragraph for your answer.
Finally, I find it comical that people refer to Andy as an “elections expert”. He’s never certified a voting system. He’s never been an election administrator. He’s never created an election management system or a voting machine. I’ve certified machines and I’ve conducted elections as an election administrator. My fellow election administrators and I are the experts, not Andy who sits back and takes pot shots without having the courage to build a system of his own. Any reasonable person who honestly believes the voting systems are as vulnerable as he says would at least create a prototype that solves these issues. Of course Andy hasn’t and never will do this. Why? Well, number one is because he can’t. Number two is that it’s not necessary for him to continue to raise his profile by scaring the hell out of the American public. Has the word coward crossed your mind yet?
Lastly, and most disgusting, is that Andy is an ableist the likes of which the election industry has never seen. In my county we have done close to 100 demonstrations for various groups that represent the disabled all across our state and many from across the country. These XL machines finally make these disabled and low literacy voters feel empowered to not only vote indeiendently, but vote in the same way on the same machines as all other voters. On the other hand, good ole Ableist Andy is perfectly fine sending disabled and low literacy voters into the corner to vote on their own machine. Andy is an elitist so naturally he feels very comfortable with a separate but equal approach to voting. I wonder if he’s against ramps into polling locations as well. If this guy doesn’t sound like a heartless Republican then I’ve never heard of one. He’s Mike Lindell under a different disguise.
Reader, take note of three things:
1) Andy will delete this post faster than you can say separate but equal because he is afraid of people learning the truth.
2) In the unlikely event that Ableist Andy leaves this post, he will of course respond. When he does, he’ll try to suck you in with obscure disputes to what is written here. Reader, all you need to pay attention to is how he plans to hack Microsoft bitlocker. If he does not make a specific claim that bitlocker can be hacked, then nothing else he says matters one ounce. As noted previously, if you can’t hack bitlocker there is precisely a 0% chance of pulling off this science fictional hack. So scan his response for a reply to the bitlocker hack. He won’t claim it can be done because it’s impossible with current technology. And if he starts spewing BS about quantum computing please feel free to make an appointment for him with your local mental health specialist.
3) Ableist Andy will go on to say how all of this is possible with an insider attack from someone who has admin credentials and a deep understanding of the hardware and software. Although I maintain it’s still virtually impossible under those circumstances, literally any system has the potential to be hacked if performed by an insider with full credentials. That goes for ALL systems and that can never be fully guarded against. Andy will go into some explanation that you won’t understand about how it’s possible to protect against the success of a havk with a hand marked ballot system but the bottom line is those machines have the same chance of being hacked by an insider as the XL machines.
Although Andy lives in New Jersey, he obviously didn’t have the courage to attempt to fight us here because he knows that we know better. Ableist Andy will not be able to terrorize our most vulnerable voters with his “separate but equal” approach to voting and his total willingness to sacrifice .5% to 3% of votes if it means he stays relevant as an “expert”.
Andy, thank God your vote for Trump will be irrelevant in my state.
Dear Replier who was so confident in his/her response that he/she failed to put their own name on it —
I don’t have time to reply in full to your grotesque comment and attack on Prof. Appel. So I’ll just respond quickly to this early obnoxious (and inaccurate) remark of yours:
“He lives in a science fiction world, as many if these silly academics do. He lives in the hypothetical world, not in the real world. In the real world, in order to pull off a hack like his fantastic and delusional scenario describes, Andy and his so-called “sophisticated hackers” would have to gain illegal access to the warehouse where machines are stored, bypassing alarms, cameras and locks.”
Perhaps you haven’t noticed, but we now have a whole bunch of Election Officials — from Colorado to Georgia to Michigan and beyond — with all of the access in the world to those warehouses where machines are stored and where bypassing security systems is child’s play. (Not that the hacks about which the Professor writes here actually require access to all or even ANY of those machines.)
So, your critique is simply wrong from that standpoint.
But, if I deign to grant your point that these sorts of hacks would require criminal masterminds with unfettered access (they don’t), there is still the problem of the fact that, with horrifically designed, wholly unverifiable and shamefully insecure systems such as these, even if they aren’t hacked (or programmed in error), the public has NO WAY OF KNOWING THAT THEY HAVEN’T BEEN.
In *your* best case scenario, the public will never be able to have confidence that their elections were tallied as per voter intent. Though, I suppose, you could show up on their blogs anonymously, one by one, and smear them. Maybe that will work!
Good lord…Fail, dude.
Brad, you fail to show intelligence with this response. Your comment about illegal access conveniently left off the sentence I wrote that acknowledge that criminal access to the machines is possible. I never used the term criminal masterminds. That is juvenile hyperbole which is very typical for you. It remains a fact that accessing these machines without permission from the county is, in fact, a crime.
Your comment “the public has no way of knowing that they haven’t been” suggests that voters won’t know a hack had occurred. Well, that’s the definition of a successful hack is it not? The point of a hack is to take actions that are not noticed by the user. You want hand counted paper ballots. Have the courage to at least admit that.
Based on your hyperbolic and juvenile claims with zero evidence or even anecdotes to support your claim, I can only conclude that you are not an intelligent man. At least Ableist Andy js smart.
Finally, I’m an elector administrator. Reasons for my anonymity are obvious to those who do not lack intelligence.
In reply to “New Jersey elections administrator”:
I find your reply to Brad Friedman to be both “hyperbolic and juvenile”, i.e. exactly what you accuse him of. There is no need impugn someone’s intelligence just because you strongly disagree with them. I know Brad well, and he is an exceptionally intelligent and articulate man.
You attack him for lacking the “courage” to “admit” that he is in favor of hand counted paper ballots. Your criticism is way off the mark however, because he has said that publicly many times. It is no secret. I don’t happen to agree with him on that point, but he has been very open and consistent about it for years.
Your understanding of security issues seems a little simplistic. You suggest that part of “the definition of a successful hack” is that the targets “won’t know a hack had occurred”. No. With denial of service attacks or ransomware attacks, for example, the targets know immediately that the attack has occurred, but the goals of the attacker are still achieved. In the case of attacks that exfiltrate personal data, it may not matter to the attacker whether the targets know it has been stolen. The data cannot be “unstolen” and the attacker achieves his goal either way. In the case of attacks that modify votes the attacker either succeeds in changing the results of the election if undetected, or completely discredits the electoral system and destroys public confidence if it is detected. Either way the attacker wins.
Finally, I find the fact that you post ANONYMOUS intemperate attacks on Prof. Appel (not “Ableist Andy”) and on Brad Friedman to be cowardly. You claim to be an “elector administrator” (sic) but I don’t see any evidence of that. Even if you are I don’t think the reasons for your anonymity are as “obvious” as you claim they are to “intelligent” people. Maybe you are suggesting you might be subject to some kind of threats if your postings here were not anonymous, but to me that sounds a little too self important on your part. Those of us who have been studying and writing about election integrity and cybersecurity for decades are also subject to threats, but we still do not publish anonymously. I suspect the more likely reason you wish to remain anonymous is the same one motivating millions of others to post anonymously on social media: the freedom to flame and be disrespectful and insulting without being held accountable. That is pretty unprofessional behavior for someone claiming to be an elections administrator.
Please dial back the sarcasm, insults, and personal attacks in your future posts, and have the courtesy and courage to identify yourself.
ES&S has provided this response to the New York State Board of Elections:
“… a printer prints the votes onto a paper ballot; the voter has a chance to review the ballot to make sure the right choices are printed; then the machine sends the ballot past an optical scanner to record and tabulate the votes. Then the mechanism drops the paper into a ballot box…”
The above is not an accurate statement. The XL scans as it prints, not after the voter chooses to cast. A reminder about how the XL behaves:
1. Prints the card and simultaneously scans the ballot to ensure printing is accurate and readable.
2. Presents the printed ballot alongside the voter’s on-screen selections to encourage voters to verify accuracy.
3. ADA Voters can have selections scanned from the paper read back to them.
4. Ejects the card at high speed.
“It seems that the engineers at ES&S read our paper, because they’ve released a redesigned paper path for the ExpressVoteXL that they claim fixes the problem. They produced this video that states their claim. Unfortunately, they’re wrong: it doesn’t fix the problem.”
ES&S is always listening to feedback, and our redesigned paper path for the XL is one of the many ways in which we have incorporated additional layers of protection in the unlikely event of an unauthorized attempt by a nefarious bad actor to manipulate a voting unit. Our re-engineered paper path design took what was already a highly improbable attack scenario and rendered it not only impractical but also nearly impossible.
“Their claim is: they have a new “one-way bearing” on their platen roller. It’s mechanically impossible for the “platen roller with one-way bearing” to print while the paper is moving down; mechanically it’s only possible to print while the paper is moving up.”
• This is not a claim. It is a fact. The mechanical design does ensure that if the print head is lowered as the paper is moving away from the voter, it will jam because the 1-way roller bearing fails to turn and push the paper through the print head.
• The 1-way bearing can best be described as a clutch that connects the paper path motor to the printer roller in one direction and does not connect when running in the other direction. Without this connection, the paper cannot move to print and will jam.
“…software could move the paper down past the print head, then take the extra step of moving it back up, while printing unauthorized votes on the paper; then move it down again toward the ballot box.”
• This highly improbable attack scenario would require full insider access and a developer level of knowledge of three independent software components.
• When initially printed, all unmarked ballot sections are marked with an X. If a selection is added, the barcode is visibly crossed out and cannot be read by the machine. And, all vote-fors have either a selection or a “no selection,” leaving no space for any additional print.
• The hack would require changes to ES&S software, the paper path driver, and the paper path firmware and would be incredibly complicated, if not nearly impossible, to orchestrate a change across all three without detection.
• In addition to a highly complex hack, the software currently prints a full image of selections all at once. To modify the software to print a change to one contest would be an extreme hack.
“…votes that count are the ones encoded in the barcode (which the voter cannot read), not the ones printed in plain text (which the voter can read but usually doesn’t bother to read).”
• There are methods for voters to validate the barcodes. Philadelphia produces a code book to allow voters to validate the barcode selections.
• Every voter can review their ballot selections by comparing the cast vote records to the printed text. A voter may-
o Read the card into a precinct tabulator and view the printed report
o Re-read the card into an XL and preview the calculated barcode against the printed card.
Other facts –
• The theories and speculations set forth in the above blog are not based on scientific or mechanical fact but rather extreme hypotheses with zero basis in reality. No such attack has ever occurred on a voting unit in any election.
On the other hand, manipulating a paper ballot is a simple proven hack that merely requires one nefarious bad actor with a pen. The XL is the most tested piece of voting equipment produced by ES&S. Multiple independent tests, including the Department of Homeland Security Idaho National Test Labs (Critical Product Evaluation Program), have confirmed that the device is safe, secure, and reliable.
I stand by my analysis: The key vulnerability is that a software hack can make the mechanical components do things out of regular order. ES&S admit this in their reply: They write, “This hack would require changes to ES&S software, the paper path driver [software], and the paper path firmware [also software] and would be incredibly complicated.” That is, ES&S says that these are the software in the ExpressVoteXL that, if hacked, would make the mechanical components behave as I described. In our modern world, we see incredibly complicated software hacks detected many times per year to commercial software, and nobody knows how many undetected ones.
When ES&S writes, such things as “the XL scans as it prints”, they are (as usual) describing what the legitimate software is supposed to do, not what hacked software might be capable of.
If you scan “simultaneously” with printing, what are you scanning? The print head? Until the head moves, the ink it’s depositing isn’t readable. The head is in the way. In order to scan what’s printed, the printing has to be accomplished, and then the scan can take place.
Testing cannot prove that a machine is “safe” or “reliable”. It can only certify that the machine is free from specific defects under test.